Enable Registry Editor, Task Manager and Folder Options
Remove regsvr.exe Virus
Microsoft Office to go online — for free

How to Reset / Recover Forgotten Windows NT / 2000 / XP / 2003 Administrator Password?
Many times we face this problem when we or our friends forget Windows XPpassword and can't log into Windows. So here we are posting a few methods / utilities which can be used to recover Windows password:
1st Method:
The first thing which you check if you forget login password. When we install Windows, it automatically creates an account "Administrator" and sets its password to blank. So if you have forget your user account password then try this:
Start system and when you see Windows Welcome screen / Login screen, press
Now you can reset your account password from "Control Panel -> User Accounts".
Same thing can be done using Safe Mode. In Safe Mode Windows will show this in-built Administrator account in Login screen.
2nd Method:
Windows XP and further versions also provide another method to recover forgotten password by using "Reset Disk". If you created a Password Reset Disk in past, you can use that disk to reset the password. To know more about it, please visit following links:
How to create and use a password reset disk for a computer in a domain in Windows XP
How to Log On to Windows XP If You Forget Your Password or Your Password Expires
3rd Method:
If the above mentioned tricks don't work, then try following trick which is actually a loophole in Windows XP Setup and a big security hole:
A. Boot using Windows XP Setup CD and follow the instruction like Accepting EULA, etc.
B. When it asks to repair your existing Windows installation, accept it and press "R" to run the repair.
C. Setup will start repairing your Windows and will start copying files, etc.
D. After a few minutes setup will restart your system and when it restarts don't press any key when it shows "Press any key to continue..." otherwise Setup will start from the beginning. Don't press any key and setup will resume where it left.
E. Now it'll start doing other tasks and will show a small progressbar with a few details in left side.
F. Look carefully at the details and when it shows "Installing devices", press
G. It'll open a Command Prompt window. Now type nusrmgr.cpl and press
H. It'll open the same "User Accounts" window which you see in Control Panel.
I. Now you can remove or reset any account password without any problem.
4th Method:
There are many 3rd party utilities which claim to recover forgotten Windows password:
Windows Geeks Lost Forgotten Password Service:
Windows Geeks have a program that works instantly to remove any lost or forgotten password. With this program you can get back in very quickly:
Windows Geeks Lost Forgotten Password Service
Emergency Boot CD:
EBCD is a bootable CD, intended for system recovery in the case of software or hardware faults. It is able to create backup copies of normally working system and restore system to saved state. It contains the best system software ever created, properly compiled and configured for the maximum efficient use.
You may download image builder utility which creates image of bootable CD-ROM (.ISO file), plus basic set of system tools. When the image is ready, write it to CD-R or CD-RW, and then everytime you'll need convenient and powerful system tools they'll be just at hand.
It is easy to customize the disk for your needs. You can include to CD any program you like, or remake the structure of CD completely. All you need is to change a few lines in configuration XML files.
Offline NT Password & Registry Editor:
This is a utility to reset the password of any user that has a valid (local) accounton your NT system. You do not need to know the old password to set a new one. It works offline, that is, you have to shutdown your computer and boot off a floppydisk or CD. It'll detect and offer to unlock locked or disabled out user accounts. It is also an almost fully functional registry editor.
Windows XP Login Recovery:
Login Recovery is a service to reveal user names and recover passwords for Windows NT, 2000, XP, 2003 and Vista. As long as you have physical access to the computer, your passwords can be recovered.
Ultimate Boot CD (UBCD): [Thanks to Rakesh for recommending]
Ultimate Boot CD runs independently of any operating system. It will boot from any Intel-compatible machine, regardless of whether DOS/Windows/Linux/BeOS is installed on the machine. However, you do need an operating system and a ISO-capable CD writer software to create the Ultimate Boot CD from the downloaded ISO image file.
5th Method:
If all fails, then simply reinstall Windows and create new accounts. To recover lost data, you can use Data recovery tools available on net but the chances will be very low to get data back.
That's all we can suggest. If you have any other method / tool, feel free to post here.
ERP at the Speed of Light
10 security threats to watch out for in 2009
New virus infects ATM , steals money from banks
The Conficker Worm
Worried about the Conficker worm striking on April 1st? A few simple steps can protect you. Target: All users of Windows XP and Windows Vista. If you’re worried about the Conficker worm striking on April 1st, don’t be. On April 1st the Conficker worm will simply start taking more steps to protect itself. After that date, machines infected with the “C” variant of the worm may not be able to get security updates or patches from Microsoft and from many other vendors. The creators of the worm will also start using a communications system that is more difficult for security researchers to interrupt. The Conficker worm, sometimes called Downadup or Kido has managed to infect a large number of computers. Specifics are hard to come by, but some researchers estimate that millions of computers have been infected with this threat since January.
What does the Conficker worm do?
We don’t know the purpose of the Conficker worm. Today the worm has created an infrastructure that the creators of the worm can use to remotely install software on infected machines. What will that software do? We don’t know. Most likely the worm will be used to create a botnet that will be rented out to criminals who want to send SPAM, steal IDs and direct users to online scams and phishing sites. The Conficker worm mostly spreads across networks. If it finds a vulnerable computer, it turns off the automatic backup service, deletes previous restore points, disables many security services, blocks access to a number of security web sites and opens infected machines to receive additional programs from the malware’s creator. The worm then tries to spread itself to other computers on the same network.How does the worm infect a computer?
The Downadup worm tries to take advantage of a problem with Windows (a vulnerability) called MS08-067 to quietly install itself. Users who automatically receive updates from Microsoft are already protected from this. The worm also tries to spread by copying itself into shared folders on networks and by infecting USB devices such as memory sticks.Who is at risk?
Users whose computers are not configured to receive patches and updates from Microsoft and who are not running an up to date antivirus product are most at risk. Users who do not have a genuine version of Windows from Microsoft are most at risk since pirated system usually cannot get Microsoft updates and patches.Advice to Stay Safe from the Downadup Worm:
- Run a good security suite (we are partial to Norton Internet Security and Norton 360).
- Keep your computer updated with the latest patches. If you don’t know how to do this, have someone help you set your system to update itself.
- Don’t use “free” security scans that pop up on many web sites. All too often these are fake, using scare tactics to try to get you to purchase their “full” service. In many cases these are actually infecting you while they run. There is reason to believe that the creators of the Conficker worm are associated with some of these fake security products.
- Turn off the “autorun” feature that will automatically run programs found on memory sticks and other USB devices.
- Be smart with your passwords. This includes
- Change your passwords periodically
- Use complex passwords – no simple names or words, use special characters and numbers
- Using a separate, longer password for each site that has sensitive personal information or access to your bank accounts or credit cards.
- Use a passwords management system such as Identity Safe track your passwords and to fill out forms automatically.
BJP's IT interest to be threat for Microsoft, telcos
 Bharatiya Janata Party's (BJP) interest on IT development may prove to be a threat for software companies like Microsoft and top local telecom firms. The opposition party's leader LK Advani has promised to vehemently promote open-source software and internet telephony if the party comes to power in the upcoming elections.
The party also plans for the release of one crore laptops with open source software to students, for which it has earmarked Rs.10,000 crore. The party also plans to allow unrestricted internet telephony. Microsoft India spokesman refused to comment on the speculations, as reported by The Economic Times.
However, many of the experts feel that this move might not have a major impact on the software giant. "Open source has been there for a long time in the market now. Any promotional thing for open source will not make any significant difference to the major players. Both enjoy a very different kind of market and there is significant demand for both," says Akhilesh Tuteja, Executive Director of consulting firm KPMG.
The IT companies in India also witness it to be a boon than a threat. "We believe the policy will help in improving IT industry in India through adoption of open standards and promotion of domestic web hosting industry. We hope other political parties will follow suit," said Sun Microsystem's country director Jaijit Bhattacharya.
Bharatiya Janata Party's (BJP) interest on IT development may prove to be a threat for software companies like Microsoft and top local telecom firms. The opposition party's leader LK Advani has promised to vehemently promote open-source software and internet telephony if the party comes to power in the upcoming elections.
The party also plans for the release of one crore laptops with open source software to students, for which it has earmarked Rs.10,000 crore. The party also plans to allow unrestricted internet telephony. Microsoft India spokesman refused to comment on the speculations, as reported by The Economic Times.
However, many of the experts feel that this move might not have a major impact on the software giant. "Open source has been there for a long time in the market now. Any promotional thing for open source will not make any significant difference to the major players. Both enjoy a very different kind of market and there is significant demand for both," says Akhilesh Tuteja, Executive Director of consulting firm KPMG.
The IT companies in India also witness it to be a boon than a threat. "We believe the policy will help in improving IT industry in India through adoption of open standards and promotion of domestic web hosting industry. We hope other political parties will follow suit," said Sun Microsystem's country director Jaijit Bhattacharya.
10 dumb things you can do to your Cisco router
Tokenless Two-Factor Authentication: It Finally Adds Up
Top 10 changes to security in Windows 7





How to fix printer job queue issues
1. First and foremost we need to stop the service which is responsible for printing. Hence hold on Win key + R to bring up the Windows Run command. Type in services.msc, press Enter. In Vista simply hit the Start Orb and type in services, click on the option to open up.
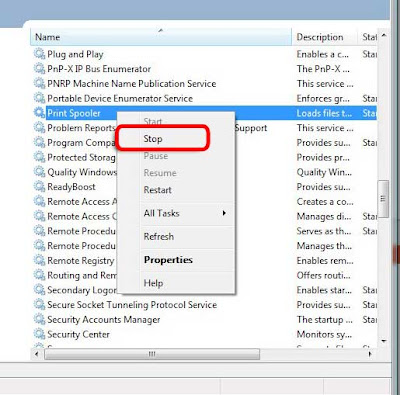
 2. Now once in the services window click any of the options on the left side, hit P on the keyboard till you come to Print Spooler option. Right-click and click Stop to disable it. You've just stoped your PC from printing anything further, but your printing job has yet to be flushed.
2. Now once in the services window click any of the options on the left side, hit P on the keyboard till you come to Print Spooler option. Right-click and click Stop to disable it. You've just stoped your PC from printing anything further, but your printing job has yet to be flushed. 3. For that navigate to C:\Windows\System32\spool\PRINTERS and delete all the contents in the folder. You've now flushed everything from you print job.
4. Back to services, now Right-click and click Restart to enable printing on your PC again.
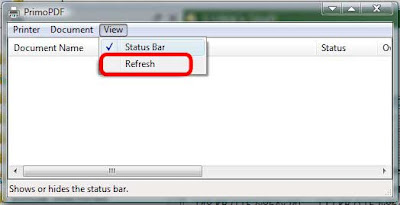
5. Refresh the print queue. Your problem should have been solved.
There's a great little freeware application called Print Flush 1.3. It's a batch file that does the same thing mentioned here with just a click of the mouse.
Make Office 2007 More Compatible
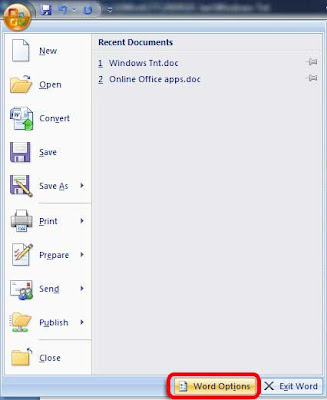
1. In Word 2007, click the circular Office Button in the upper-left
2. Now press Word Options
3. Click Save on the left.
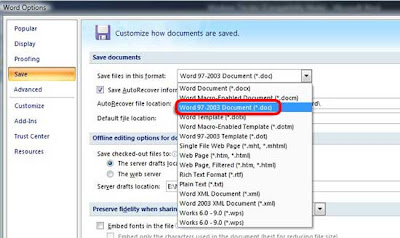
4. On the right hand side now you'll see Save files in this format
5. From the drop down menu select Word 97-2003 Document (*.doc)
Now all your saves by default will be in .doc format that is unless you are already working on a .docx format. The same process applies for Excel 2007 and PowerPoint 2007.
Make Adobe Reader Remember Last View When Re-Opening files
1. Open Adobe Reader, click on Edit | Preferences
2. You should be in Documents category, if not then click on it.
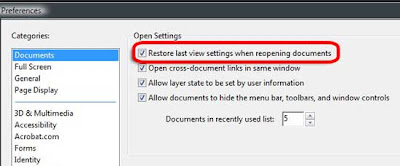
3. Click on Restore last view settings when reopening documents.
That's it you are done. Now go to any page, close a PDF document and open it, your last viewed page will be remembered even if you change the location of the document.